Gallery
 Virus Incidents in Hong Kong hi-res
Virus Incidents in Hong Kong hi-resI am going to talk about the changing anti-virus situation today:
First I will discuss what we are seeing in Hong Kong today. This is mainly a summary of the paper I delivered at the Virus Bulletin Conference last week.
From that we will see that boot sector viruses are causing the majority of infections, even though they are easily preventable.
This will lead to what an organisation needs to defend against viruses.
Then, I will discuss macro viruses, that have received a lot of publicity in the past few weeks.
Finally, I will hand over to Savio Chan, who will explain some of the features of F-PROT Professional that are advantageous in an organisational setting.
We will be asking some questions during the talk, and giving away these very nice T-shirts, so please keep awake!
What viruses have been seen in Hong Kong?
This is a table compiled from samples I have been sent. But there are viruses here that are quite old, and new viruses that have never been seen "in the wild". So what viruses are you likely to find attacking your organisation in Hong Kong? This is a shorter list of cases where the virus seemed to be spreading. This reflects the international situation, most actual virus incidents are caused by a small number of viruses:
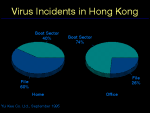
Even more significantly, if we look at the numbers of boot sector and file viruses we find most incidents are caused by boot sector viruses (fig. 2). Note here that file viruses are more common in a home environment. If you think about how file viruses are transmitted, an executable file must be transferred, it becomes clear why this is so, business users exchange documents frequently, but programs rarely. Home users are often enthusiasts who freely swap programs, often via BBSs with people they do not know.
So, the type of virus you are most likely to meet attacking your organisation is a boot sector virus. As we move on to discuss why this old virus type is still such a problem, lets have a couple of questions:
So what is going on? The problem is that most users are not aware of these two simple points, so they continue to forget to remove disks before booting, and, once they have booted and got the "Non-system disk or disk error" message, they take the disk out and continue without checking to see if they have just infected their machine.
Viruses are a concern for the whole organisation, and should be planned for accordingly.
Appoint an Administrator: This person will be responsible for the day-to-day monitoring of viruses in the organisation. He will have detailed knowledge of how viruses spread and the risks posed by different sorts of infection. This is a similar position to a fire safety officer, who may order people out of a building in an emergency. The anti-virus administrator has high authority and may order computers to be quarantined or shut down.
Prepare the Anti-Virus Strategy: The administrator will have a major input into this.
Choose the anti-virus software: Apart from the obvious criteria of detecting the most viruses, also consider the features that make it easier to administer the situation throughout your organisation: Can updates be distributed automatically, can the administrator receive reports from infected machines automatically, can it be configured to scan without user intervention? Does it fit your anti-virus strategy?
Implement basic precautions: Backups are a traditional method of data protection that are still useful in protecting against viruses, but if a machine has been infected for some time, all the backups could be infected as well. We will see in a minute a very effective trick to use against boot sector viruses.
Define the role of staff: write an Anti-Virus code (fig. 4) This must be clear and simple, here is an example.
It is the responsibility of all computer-using employees to watch for computer viruses and prevent their spread by following this code:
Train staff: For most staff, a one-hour session that introduces the dangers of viruses, the company anti-virus code and the basics of the anti-virus software chosen could be sufficient. Other staff, particularly technical staff, would require more training. Their position of power, particularly in a networked environment, makes it more devastating when their machine is infected. (a properly configured network is quite resistant to virus spread, until the supervisor logs in and executes an infected program!)
Keep aware of the threat: Monitor the number of incidents, and be aware that viruses are a moving target, in a minute I will talk about a new class of virus that changes the way you need to think about viruses.
We have already said that over 70% of incidents are caused by boot sector viruses, I will now explain a trick that can protect you against these infections at (almost) no cost.
Boot sector viruses infect your hard disk when you boot from an infected diskette. This usually happens accidently, when a diskette is forgotten in drive A: while the machine is switched on. Avoid accidently booting from floppy disks. Original PCs always looked for a disk in drive A: before trying to boot from the hard disk. Most PCs now allow the boot sequence to be set, this is done in the Setup options, and is called something like:
Initial System Load: Fixed/Diskette
or
System Boot Up Sequence C:, A:
When set correctly, the system will always try booting from the hard disk first, ignoring any floppy in drive A.
This is not a perfect solution. It does not detect or remove the infection, it just stops it spreading onto a machine. But cleaning one diskette is simpler and quicker than cleaning a hard disk and that means saving money for your organisation. You had better not use this as your only means of anti-virus defence, but it is a useful component.
The new threat is actually quite old, anti-virus researchers first discussed the possibility about five years ago. The only surprising feature is that it took the virus writers so long to find the idea.
It was the Winword.Concept virus that hit the news a few weeks ago, but since then, two other macro viruses have been found. One of them attempts to drop a conventional file virus, it fails, because there are three programming errors, but these could all be fixed quite easily.
There are a number of important points:
Users can assist in this, ask your application developer to:
Macro viruses change the way we need to think about viruses. We used to say that viruses cannot spread from data files, and you cannot spread a virus just by reading email, you must execute something. Viruses can now infect documents, because a document can contain executable macro code. Viruses can infect your system when you read email, if someone sends you a document via email, your mail reader might automatically start an application when you read that, so a macro virus can infect your system just when you read mail. Confusingly, the line between data and programs and the line between reading and executing has been blurred, a document can contain executable code, and a mail read may imply execution of an embedded macro.
| Old Rule | The Change | New Rule |
|---|---|---|
| A virus cannot spread from a data file | Documents can contain executable code | Macro viruses infect documents |
| You cannot spread a virus just be reading email | Mail readers start viewers automatically | Macro viruses can spread when you open an infected message |
Macro viruses are a problem for hardware card manufacturers, the current cards are unable to capture them, and it would be difficult to redesign the cards. I would also be interested to hear the response of any anti-virus vendor who used to claim that their product "Never needs updating". Anti-virus development is not just a matter of adding search strings for new viruses, sometimes there are developments in the viruses being produced that require a rethink in the methods being used.
The objective of every organisation is to reduce the cost of virus incidents. This goal can be achieved by implementing a suitable anti-virus strategy. Good anti-virus software is one component of the strategy. Savio Chan will now introduce some of the features of F-PROT that are useful in an organisational approach.