Gallery
 Map of China, showing Beijing, Shenzhen and Hong Kong hi-res
Map of China, showing Beijing, Shenzhen and Hong Kong hi-res Fig. 2: Screenshot of Shatin virus hi-res
Fig. 2: Screenshot of Shatin virus hi-res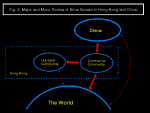 Fig. 3: Three environments for virus spread hi-res
Fig. 3: Three environments for virus spread hi-resDuring the past two years, a number of viruses have emerged from Hong Kong and China to spread internationally, and others are only known locally. Hong Kong and China are simultaneously very close and widely separated in terms of business, communications, technical knowledge and availability of computing power.
The types of virus written and their spread are dependent in different ways on the environments in the two cultures. This paper will look at the viruses written and relate this to what is known about the virus writers and virus writing groups in Hong Kong and China.
The differences in virus reports from business and BBS users in Hong Kong show that different viruses are suited to spreading in these environments. Corporate indifference and teenage irresponsibility contribute to the virus problem in different ways.
I think everyone knows that Hong Kong is a major international finance center and the biggest entry port to China. How do viruses fit into this environment, and what effect does this have on the international virus scene?
Change is dominant. For Hong Kong, 1997 will mark the end of British rule and preparations are being made throughout society. In China, use of computers is growing enormously, last year the estimated number of PCs in China was one million, this year it is double and the growth will continue.
Relevant laws exist in HK & China. HK has the Computer Crimes Ordinance, introduced in 1993 , the first case prosecuted under this was a cracker earlier this year.
In China, the National Congress issued a Guideline in February 1994 . This places the Ministry of Public Security in charge of the whole nation's computer information systems security. More specifically, this Ministry is given responsibility to manage research and investigation of "computer viruses and other data endangering social and public security and related harmful programs". In addition, a permit is required for selling products specifically designed for computer information systems security. The permits are also designed and administered by the same Ministry.
Paragraph 28 of the guidelines makes two definitions: A computer virus is a program or programs inserted into computer programs, that can destroy the function of the computer and or destroy data or influence the function of the computer, it is also a program that can be self-replicating. This definition appears to cover most malware: viruses, trojan horses, logic bombs, and maybe even buggy programs.
Secondly, a specialised computer information security product is hardware or software products specialised in protecting computer information system security.
Paragraph 23 of the guideline specifies punishments: Deliberately introducing computer viruses or any other harmful data that endangers computer information system security, or selling a computer information system security product without a permit can result in a warning from the Ministry of Public Security or a personal fine of up to 5000 yuen. Organisations may be fined up to 15000 yuen. Any gains from the violation would be confiscated, and there can be a fine of from 1 to 3 times the quantity gained. As a comparison, the average monthly salary in China is 200 to 300 yuen, although anyone privileged with access to a computer could have a much higher salary.
This leads to a curious situation. People who spread viruses do not gain from their actions, so the penalty for selling a security product without a license is potentially higher than the penalty for deliberately spreading a virus. It seems that the National Congress failed to understand the nature of the problem when it issued this Guideline. The level of the penalty is also lenient for a country where corruption can be punished with the death penalty. For comparison, deliberately spreading a virus in Hong Kong can be punished with up to 10 years imprisonment.
However, the level of punishment is irrelevant when no prosecutions have been brought in either jurisdiction.
I have compiled a list of viruses for Hong Kong and China (table 1), this is different from my submissions to Joe Well's In the Wild list because I have used a slacker criteria for inclusion: I must have received a sample of the virus from someone in Hong Kong or China. Some of these I received in collections, some I received via local BBSs, and while I could see that they were spreading, I could not confirm a single case of infection. Rather than indicating the viruses in the wild, this list indicates the viruses that are "available", some of the older ones were probably in the wild in the past, the newer ones may turn out to be mere zoo specimens or the first indications of a wider spread.
The list is short, just 52 viruses for Hong Kong, and a handful for China. It is almost certainly incomplete, the China list should improve as stronger links are forged. For Hong Kong, it is possible that my contacts are insufficient, but it probably also be because the local "virus collector" community does not have frequent exchange with their European and American counterparts. This brings us to communications.
In Hong Kong, local phone calls are free, and, as HK is a small territory, everywhere is local. Consequently, there are large numbers of Bulletin Boards. However, international calls are expensive. A recent change is in access to the Internet. The first Internet Service Provider opened in 1994, and interest has rocketed in the last 6 months, whether this vastly cheaper method of reaching international sites will result in a wider range of viruses in Hong Kong zoos remains to be seen.
On the BBSs, there is a well-established Virus Echo, which is unmoderated. Most of the messages deal with combating viruses, but some are from self-proclaimed virus authors (fig. 1 is part of a typical message).
Fig. 1 Part of message from a "virus writer" on HK BBS virus echo
PUBLIC Message from ***** *** to **** ***.
Source: *******; Conference 4 (V-Viruses); Message No. 8601
Time Stamp: 09-03-95 20:27
Subject: Form Virus
So.. do you know I created my OWN virus?
It is called the Jason virus... I am working on the Jason II virus...
It is REALLY strong...
I use CLME object tool and file emmbeding to create a fully pylomorphic virus.
There are NO symptoms... no one knows if he/she is infected.
It infects EVERYTHING... boot sector, files (even data), overlays, ect.
It is like the HKVTECH... infact, so of the technology used is from the
HKVTECH. Files cannot be protected at all... even attrib cannot help. MY virus
slowly uses Low Level Format... it also uses the LATEST technology...
There are hints in these messages that virus exchange BBSs exist, and some indication that there might be one or more virus writing groups, but I have been unable to verify this.
The virus writers take advantage of the BBS rules to spread their creations. Many of the BBSs specify an upload-download ratio, and check uploaded files against files already on the BBS. Uploaders of new versions may also be awarded with extra privileges. As soon as a new version appears on one BBS, users will race to be the first to upload it to all the other BBSs they know. The virus writer merely has to infect a well-known package, give it a new version number and upload it to one or two BBSs with a tantalising description. The ensuing confusion will obliterate any trail to the instigator.
Some of the virus families that have emerged from the local BBSs are:
The first in this family was Jerusalem.HK.2358, and it appeared in March 1994. It displayed the text string "HKs Vtech", which led to it being called Jerusalem.Vtech. This was later changed to Jerusalem.HK because a company manufacturing computers and other consumer electronics in Hong Kong is called Vtech. There is no connection between the company and the Jerusalem.HK family of viruses.
Jerusalem.HK.2880 appeared in May 1994, .2886 and .2513 soon followed. These were initially distributed using the "trojanised new version upload" method. By June, reports of Jerusalem.HK.2880 were circulating Dutch BBSs. This is certainly a distribution method that can be very effective.
The .2880 and .2886 variants, after displaying "HKs Vtech", also say "using VTME v1.11" and "Please ask S-S Chan to help you!". These are polymorphic, and it seems likely that VTME is the name of the mutation engine developed for this family.
Ming.1017 was first found in January 1994 and contains the text message:
Nice To Meet You! Copyright(c) 1-11-1993 By Ming. From Tuen Mun, Hong Kong
Version 3.10
It is a simple, overwriting file virus and is only notable because a minor variant reached Lapland two weeks later on video driver diskettes that had originated in Hong Kong. Even something as obvious as an overwriting virus can spread internationally with a lucky break.
In April, messages appeared on the local virus echo claiming to be from the Ming who wrote this virus. He said that he was changing his name to Crazy_Lord, and he had written CLME, the Crazy Lord Mutation Engine. Different messages mentioned versions 0.5 and 0.6. He also thanked "HKs Vtech" for assistance and challenged "S-S Chan" to kill it.
It was July before a sample of a CLME virus was obtained. The decryptor used a simple XOR loop with a variable amount of junk code.
Ming.CLME.1952, Ming.1017 and Ming.CLME.1528 increased in samples uploaded to my BBS the following months, and are still occasionally uploaded now. A total of five Ming viruses are currently known.
The author appears to be a novice programmer, improving his skills with practice. The collaboration between him and the author of the Jerusalem.HK family can only be guessed at.
Shutdown.644 appeared in January 1994. It contains the text message:
Computers must be shut down to dedicate my sister
Reports of it, and a second variant, .698, have appeared sporadically in the BBSs until recently.
Two other viruses known in Hong Kong BBSs are notable because they display, or attempt to display, a message in Chinese characters.
Jerusalem.J uses DOS calls to redefine four characters as two Chinese characters "Death God". The display routine fails on some video cards. It first appeared in October 1994. Interestingly, in November 1994, a message complaining that it had been named wrongly, and was actually called "Jerry virus" was posted in the local virus echo. The writer of the message claimed it was not related to Jerusalem because it "only has 30 bytes like Jerusalem".
Shatin takes a different approach to displaying Chinese characters. It uses block graphics to make the Chinese characters for "Forget me not" as a full screen display (fig. 2). It appeared in February 1995.
All these viruses have been widely reported in the local virus echo, but there have been no local reports from commercial sites.
I had hoped to give a detailed profile of Hong Kong virus writers, but firm evidence has not surfaced. The impression from numerous BBS messages is of a small number of actual writers, probably adolescent male, and a larger number of wannabe virus-writers and hanger-ons. One correspondent at different times claimed to be a virus writer and to know a virus-writing group, but not be a writer himself. He claimed to be concerned what the group would do to him if he revealed what he knew. I could not work out if he was trying to fool me, or if he was really worried, or even if the messages originated from one or more people.
The commercial companies have more international interchange.
Literally thousands of Hong Kong companies have offices or factories in China. It is easy to imagine that this provides a channel for viruses written in China to reach the International scene. Two specific incidents suggest, but do not prove this:
In March 94, within a couple of weeks, I received two samples of AntiCMOS.A. One was from an airline, the other a manufacturing company. Both believed that the virus had come from their China branches. These were not the first samples of AntiCMOS found internationally, but they were close to that date.
The next stage in the chain is a company without an antivirus policy. In April 94, I received a sample from a large local bank. In May, a salesperson for an online banking service from that bank was found to have an infected demonstration diskette. The diskette in question was not write-protected, and the salesperson's standard procedure was to use a customer's machine to do a directory of the diskette, and then to boot the machine from it. This procedure seems designed to maximise the chances of picking up an infection and distributing it to the maximum number of customers. Since then, reports of AntiCMOS have risen.
I have had only one sample of AntiCMOS.B, in early May 94. This was collected from a computer company in Shenzen. This variant contains the text "I am Li Xibin". Li Xibin is a plausible Chinese name, that and the dates of first appearance suggest that AntiCMOS is a Chinese virus.
This was first found in January 1994 in a manufacturing company with a branch in China (as labour costs rose in Hong Kong, many companies moved their factories to China, and kept their head office in Hong Kong). Again, the possibility that this had traveled from the Chinese branch was mentioned. It spread in Hong Kong in the subsequent months. A trip to Beijing at the beginning of August 94 showed it was well-known there. Several samples were received, and local anti-virus software detected it as DA01.
Near the end of August, it leaped to Norway via video device driver diskettes duplicated in Hong Kong.
China itself requires a lot more research, but of the ten viruses found, six have not been seen elsewhere. Of the others: AntiCMOS.B was found almost simultaneously in China and elsewhere; Mange-tout we have already mentioned; Hidenowt was found in Hong Kong soon after it's original discovery and Chinese anti-virus software recognises it with the name of "Dong"; and Changsha contains a name and address in China. A perception noted in China was that foreign anti-virus software is unable to detect Chinese viruses, this sample shows how that idea could arise.
The Chinese anti-virus software mentioned is called Kill and is produced by the Ministry of Public Security. It used to be distributed free, but it is now being sold. The apparent conflict of interest between the same organisation having responsibility for issuing permits to sell security software, and selling it's own security product, does not seem to be a concern.
In Hong Kong The corporate and hobbyist appear to form two separate environments (fig. 3). The corporate environment has more frequent China and international connections, but largely only exchange data diskettes. Thus, boot sector viruses are dominant. This is assisted by the failure of many corporations to take the simplest of precautions.
The hobbyist environment frequently exchange files on BBSs, but these will generally be entirely within Hong Kong. So, file viruses are common, and locally written viruses are well represented, but some viruses well known internationally are missing. This may change as the Internet boom allows exchange between previously isolated collectors.
China is largely isolated, but has it's own virus writers. Who they are and why they write is currently unknown. However, it seems certain that we will encounter more from China as it develops and increases links.