Gallery
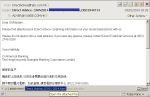 Transaction Advice Email hi-res
Transaction Advice Email hi-res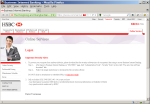 Security Advice on Logon Page hi-res
Security Advice on Logon Page hi-res "Secure Envelope" asking for password hi-res
"Secure Envelope" asking for password hi-res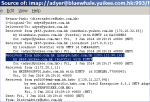 Email Headers showing sending server address hi-res
Email Headers showing sending server address hi-resFirst published: 07th March 2014
Allan Dyer
One of the most persistent vulnerabilities in information security is the end user. End users can be socially engineered into taking all sorts of unwise actions; such as selecting weak passwords, revealing sensitive information, or compromising their computers by opening suspicious attachments or following suspicious links. Educating users is a continuing challenge, and to have any chance of success we need to present simple, consistent rules for users to follow.
This makes my recent experience as an end user of online banking services at a major bank somewhat disappointing.
I received an email notifying me about recent transactions for a commercial bank account I manage. The email claimed that the information was in the attached file. Is this suspicious?
Behaving as I would advise a suspicious user to behave, I typed the URL of the bank into my browser and looked for their advice about emails. On the logon page I found the clear instruction:
DO NOT clicks on attachments or embedded URLs in suspicious emails.
Note that my browser has highlighted the name of the bank with a green background, indicating that the website has proved its identity with an Extended Validation SSL certificate.
Then, acting as I would NOT advise a user to behave, I opened the attachment. It showed a webpage with the title "Secure Envelope" asking for my password. There is no indication to the end user why this is a Secure Envelope, or any assurance that it came from a trusted source.
I decided to report the email to the bank, so I called the hotline number on my bankcard (no point in calling the number listed in the email, that might be answered by a fraudulent sender). When I explained about the email, the hotline staff told me that:
However, I had also examined the email headers. Almost everything in an email message can be easily forged, but the Received: header lines are added by each server the message passes through, so, by looking at the Received: header added by your gateway mailserver, you can identify the address of the computer that sent the message with a good degree of assurance. The relevant Received: header of this message (highlighted in the image) shows an address of the bank. Therefore, either the message was genuine (and everything the hotline staff had told me was untrue), or the bank had a major security incident and criminals were using bank systems to send unauthorised messages.
In a follow-up email, I provided a copy of the suspicious message and asked the questions:
The bank replied in a phone call, confirming that the message was genuine. They also clarified that the password to access the Direct Advice was not the eBanking password, but a distinct PIN just for this purpose. Finally, they could give me no feedback from the related department, because they don't talk to customers directly.
To be clear, being notified when there is an incoming payment is a service I find useful. However, when I selected that service on the bank website, I did not expect the notification to be delivered in a manner that the security advice on the same website and from the hotline staff said was suspicious. Unauthorised access to a payment notification does not sound particularly dangerous, but a criminal could craft a similar notification that asked the user to install a new [fake] security certificate, thus compromising all future communication with the bank.
Successful user education depends on supplying users with simple, consistent rules they can use. The bank here has failed and is therefore putting their customers at risk.