First published: 26th April 2016
We are often told to watch out for suspicious emails, but what is suspicious? Could you tell the difference between a real and fake notification from your bank? This challenge uses a real and a fake notification "from" HSBC bank to a 'Business Direct' account holder, see if you can tell which is which. Black rectangles have been used to obscure customer information in the screenshots.
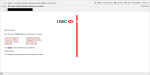
Notification A
This email:

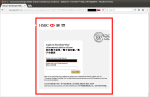
Has a link to this webpage:
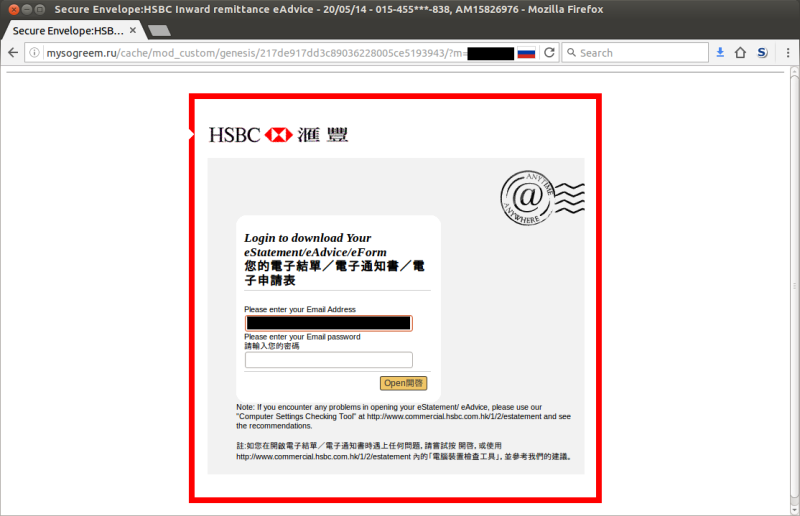
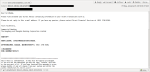
Notification B
This email:
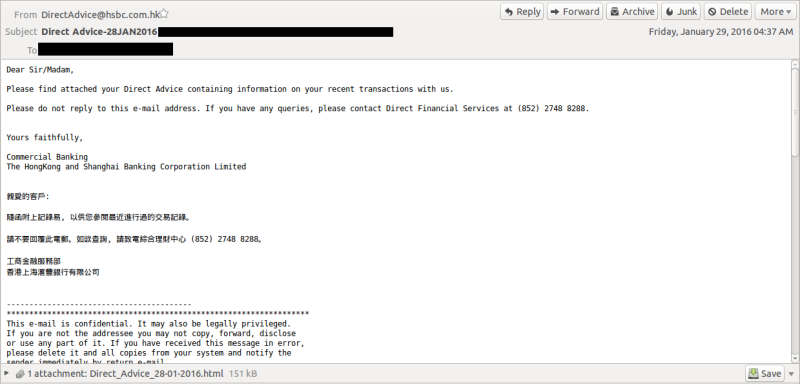
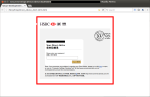
Has this webpage attached:
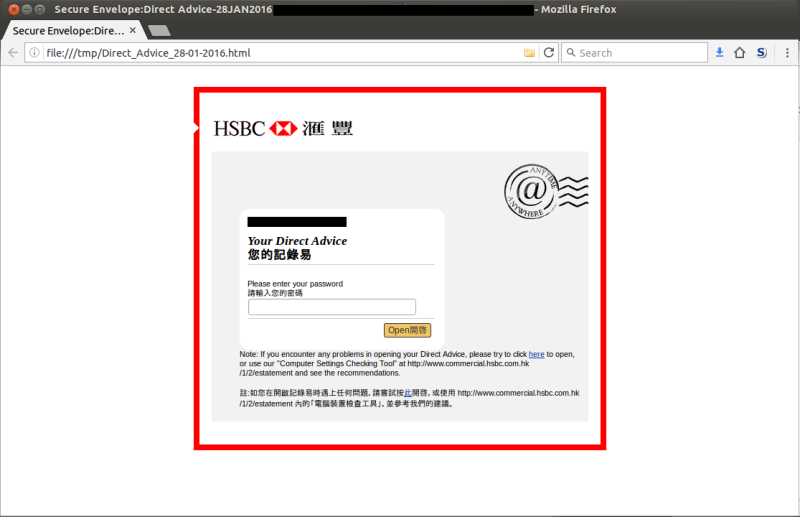
What is the Risk?
HSBC Business Direct accounts use a security device that generates six-digit codes that must be used in conjunction with the user's password to log into the HSBC website. Neither of these notifications asks for the security device code, so not enough information is collected to enable unauthorised transactions. However, this does not mean the money in the account is safe, this may be the first step of a multi-stage attack. Alternatively, the target might not be the HSBC account at all, but the victim's email account.
The Answer and Comments
Notification A is the fake. What doesn't help us distinguish between them?
- The title of both webpages starts, "Secure Envelope:". For the genuine page, this has some meaning: the attachment is encoded so that the correct "Direct Advice" password must be entered for the transaction details to be seen, but there is no way to verify that it is a "Secure Envelope", any webpage can start their title with that text.
- The fake webpage title includes, "015-455***-838" - this looks like a partially-obscured account number, and all HSBC Business Direct account numbers end in -838. Think carefully before assuming, "it knows my account number, therefore it's genuine".
- Corporate Branding: The webpages are very similar, using the HSBC logo, the "Anytime, Anywhere" postmark image and even the notch in the red border next to the logo. The fake uses the same branding in the email, so it might appear more genuine than the real thing.
What might help:
- Familiarity with the genuine article. This fake asks for the user's email password instead of the 'Direct Advice' password, the email message is HSBC branded, not plain text, other text details are different. These changes from the familiar might help the user become suspicious of the fake. Unfortunately, HSBC has not published detailed examples and made clear statements like, "this is how we do these messages, we will not change without notifying you first", so users can be easily misled by "improvements".
Checking the email headers. The real message includes the header line:
Received: from hsbc.com.hk (psmtp6.hsbc.com.hk [203.112.90.16])The equivalent line in the fake is:
Received: from srv-01.hostcloud.vn (unknown [210.86.239.114])Why would HSBC be using a cloud server in Vietnam instead of their own server? Unfortunately, this method requires some technical knowledge (which header line to look at and why?, how to interpret the line) and might still be unreliable.
- Understanding the URL. The fake webpage URL starts:
http://mysogreem.ru/cache/mod_custom/genesis/217de917dd3c89036228005ce5193943/Why would HSBC use 'mysogreem.ru' as their web server? The real webpage URL is:
file:///tmp/Direct_Advice_28-01-2016.htmlThis doesn't reassure us, the page is just a temporary file created from the email attachment, any email could create a similar file. This test might reveal a fake, but doesn't tell us what is genuine, and it may be too technical for an ordinary user.
- Checking where the webpage is served from. A neat Firefox extension, called Flagfox, helps with this. Flagfox adds the national flag of the location of the web server. This can be seen in the screenshot of the fake webpage, where it shows the Russian Federation flag. For the genuine webpage, it shows that it is a local file. Like the preceding test, this might reveal a fake, but doesn't prove the genuine. It is easier for an ordinary user to understand.
In this case, if the fake notification successfully tricks the end user, the attacker will have access to their email account. HSBC is not responsible for keeping your email account secure. However, Banks might benefit from taking a wider view of helping their customer's overall security. Very often, when looking at suspicious messages, we are not certain about the attacker's ultimate objective. In this case, if the attack is successful, the attacker will be able to access the victim's email account, and will know they have an HSBC Business Direct account. How will they seek to monetise that information?
Updated: 06th May 2016
Commercial Banking at HSBC commented:
We would like to explain that protecting our customers' information is our main priority.
If you receive any suspicious e-mail in the future, please report to us by sending e-mail to [commercialbanking@hsbc.com.hk] or call our Commercial Banking Service Hotline on (852) 2748 8288, press #-7-6 after language selection.
Updated: 13th June 2016
In a further reply, Commercial Banking at HSBC added:
We would like to explain that protecting our customers' information is our main priority.
You can refer the following links for more details:
[www.business.hsbc.com.hk/en-gb/resource-centre/online-security]
[www.business.hsbc.com.hk/en-gb/hk/campaign/cyber-crime-protection]