First published: 01st March 2018
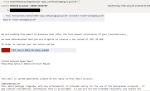
A fake tax refund email linking to a website imitating the Hong Kong Inland Revenue Department (IRD) style and requesting personal data has been received by a number of Hong Kong recipients.
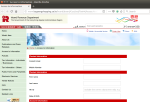
The message informed the recipient that they were eligible to receive a tax refund and should follow a link to receive the tax return[sic] online. The webpage, hosted on a Korean shopping mall website and still accessible at the time of writing, uses the Inland Revenue Department logo and style, and asks for personal and credit card information, including the CVV number. This could be used to make fraudulent charges against victims' credit cards.
There are many clues that this is a fraudulent message:
- Tax authorities do not often make unrequested refunds to taxpayers. This alone should make most recipients suspicious.
- Various text errors in the email: 'fiscalactivity' should be two words, using 'tax return' instead of 'tax refund'.
- The email From address is egis_notification@ogcio.gov.hk, but the has its own domain, ird.gov.hk, and routinely uses it for sending messages.
More technical recipients might note further clues:
- The message was sent from 32063.hostserv.eu [185.178.192.43], a server in Switzerland.
- The link points to http://primobaciobaci.co.kr//wordpress/wp-content/plugins/hello2.php, which is not a Hong Kong Government website.
- The link redirects to http://www.bupyongshopping.co.kr/board/board/Cust/sol/TaxHK/Access.html, an apparently unauthorised page on the aforementioned Korean shopping mall site.
- Other pages on the Korean shopping mall site also show distinct signs of unauthorised activity. The page http://www.bupyongshopping.co.kr/board/board/ contains a hacker pseudonym and an obscenity directed at Korea.
Could the Hong Kong Government do more to block similar fraudulent emails?
The message was sent with the envelope From of www-data@ogcio.gov.hk, from the host 32063.hostserv.eu [185.178.192.43]. The Government has published SPF records for OGCIO:
ogcio.gov.hk text = "spf2.0/pra include:spf-2.im.cis.gov.hk include:spf-2.egis.gov.hk include:spf-2.ogcio.gov.hk include:sentry-eds.com ~all"
ogcio.gov.hk text = "v=spf1 include:spf-1.im.cis.gov.hk include:spf-1.egis.gov.hk include:spf-1.ogcio.gov.hk include:sentry-eds.com ~all"
And IRD:
ird.gov.hk text = "spf2.0/pra include:spf-2.im.cis.gov.hk include:spf-2.egis.gov.hk ~all"
ird.gov.hk text = "v=spf1 include:spf-1.im.cis.gov.hk include:spf-1.egis.gov.hk ~all"
These records clearly specify which servers are permitted to send email for those departments, and they do not include the server the fraudulent message was sent from. Therefore, receiving email servers can check the SPF record and decide to reject the connection.
However, the Government has chosen to specify '~all' in the SPF records. This is a policy recommendation for the recipients of softfail: i.e. to allow mail whether or not it matches the parameters in the record. A softfail policy is usually implemented for a transitional period, while an organisation is still working on ensuring all its email users are following its policy.
Perhaps it is time for the Hong Kong Government to change its SPF policy to '-all', a hard fail.