Gallery
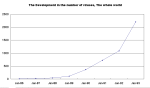 Figure 1: The Development in the number of viruses hi-res
Figure 1: The Development in the number of viruses hi-resBy Allan George Dyer M.Sc.(tech), B.Sc.
In the past seven years, computer viruses have escalated from an obscure research topic to an issue everyone has heard of, even if few understand it. Newspapers predict doom for computer users as Friday 13th or March 6th (Michelangelo's birthday) approaches. Users panic and blame every bad event, from mistyping a vital command to power surges or a floppy disc damaged by careless handling, on a virus. Consequently, many computer professionals judge the threat posed by viruses to be minor and adequately dealt with by other security measures.
How valid is this viewpoint? Certainly, the numbers of types of computer virus has grown enormously since Fred Cohen first used the term to describe self-replicating programs in 1985 (fig. 1). Today, there are more than 3000 viruses that infect DOS computers. There are also a smaller number of viruses that infect other microcomputers, including Macintosh and Amiga. Many of these are minor variations, often designed to avoid detection by particular scanners. However, the numbers still indicate that a substantial number of people are motivated to spend time with the intention of changing the operation of peoples computers, possibly in a deliberately damaging way.
Viruses, however, do not have the earth-shattering consequences described by the popular media. Although most people known someone who has been infected by a virus, the incidents were usually dealt with easily. In a questionnaire circulated at the SEARCC'93 exhibition, only one respondent had not heard of computer viruses and many had had an infection on their machine. Some said there had been no significant damage as they had simply reformatted their hard disc, neglecting the cost in human time reinstalling software, which will be significant when summed across a corporation. In the same survey, when a respondent could remember the name of the virus that troubled them, it was one of half a dozen that are known to be common worldwide (Stoned, Form, Jerusalem, Michelangelo, Monkey). Why are most infections caused by a very small number of viruses when there are so many types known? Partly it is the infection and damage strategy used by the virus, viruses that cause damage quickly are noticed and anti-virus software is updated to deal with them. A virus that spreads quickly is likely to leave clues that lead to it's discovery, but a very slowly spreading virus will not have spread far when it is discovered. A successful virus strikes a balance and achieves epidemic growth, but, possibly more important, is luck, such as infecting the source disc that will be copied thousands of times and distributed to users.
It is difficult to get well documented reports of infections in companies, especially large corporations. This is not because incidents do not happen, but because they usually happen in a minor and unmeasurable way. Typically, if a PC becomes infected, the user will start getting unexplained errors, and will, eventually report the fault to the EDP Department. A technician is sent out, who finds the virus, eliminates it from that PC. Later, another PC becomes infected, perhaps by a floppy disc infected by the first PC but missed in the disinfection and the cycle repeats. The cost is in time wasted by the user trying to work on a malfunctioning machine, and waiting for the technician, and the technician's time fixing the problem. A company with good general computing procedures is unlikely to suffer a major loss of data because regulations restricting the transfer of programs and data will slow the spread of viruses and backups will exist. However, there will be a continual slow waste of time that is ultimately costly.
A few large virus incidents are well-documented, one of the most recent is also the world's largest case of an inter-company virus infection known to date [Source: F-PROT 2.09 Version Bulletin, Copyright 1993 Data Fellows Ltd, Finland, reprinted with permission]. It occurred in the United States on March the 13th 1993. The Michelangelo virus infected approximately 20,000 computers in one corporation. A program, which was to be distributed to users, was copied to diskettes on a contaminated computer. All the 6,500 diskettes used in the copying were infected. These diskettes were then distributed to users inside the company. Due to the memory requirements of the program on the diskette, users were instructed to boot their computers directly from these diskettes. Since Michelangelo is a boot sector virus, it infected the hard discs in all the computers during this booting. The virus infected initially about 7,000 computers, but it was not detected until the number of contaminated computers had reached approximately 20,000. The company also passed the infection to some of its partners. The virus was eventually removed using the F-PROT anti-virus software.
At the time of the infection the company had no anti-virus software in use. The entire incident could have been avoided if even an anti-virus program had been installed on only the computer used for copying.
Even though an infection involving 20,000 computers is a serious matter, the situation could have been worse still. If the incident had happened a week earlier, it would have coincided with Michelangelo's activation day, in which case the virus would have wiped the hard discs empty instead of just infecting them.
Educational establishments, such as Universities have special problems, students are responsible for their own data and staff value their academic freedom. Some students are budding computer experts, eager to test the machines to their limits, others are complete novices, interested only in completing their thesis before the deadline. Many PCs are not "Personal" Computers at all, but a shared resource that may be used by many people during a day. This provides a very fertile environment for the spread of viruses. In my experience at London University some Colleges had an endemic problem with a particular virus, all the public computers were infected and each time the Computing Services staff disinfected one, it would be quickly reinfected from an infected diskette held by an unsuspecting student. The problem was dealt with by a virus awareness campaign and distribution of anti-virus software, but it was still several months before the number of reinfections dropped to a low level. In effect, the diskettes kept at home by students acted a reservoir of infection in exactly the same way as is found in some biological diseases.
Companies often believe that they need not take specific precautions against viruses because their other security measures are sufficient.
Firstly, a policy of not using unauthorised diskettes or programs is thought to prevent entry of a virus to the company: the closed computing environment. Users do not bring games from home or swap dubious shareware utilities, where many infections are believed to originate. There are two flaws to this:
Major computing manufacturers recognise that a "closed" computing environment is not sufficient. IBM operates a closed environment, but also writes its own anti-virus software. Intel, DEC and Hewlett-Packard all license anti-virus software for their use.
Secondly, good backup strategies are believed to allow recovery of all important data, anyway. Again, there are flaws:
Making frequent backups diminishes the danger of a total disaster in the case of a virus attack, but since even copies can be infected or corrupted, other measures are needed.
Effective protection against viruses involves using several methods in an overall strategy. Like any defence system, different parts have diverse strengths and weaknesses, and only a combination of techniques can give a secure whole.
Education is one of the primary techniques. In situations where technical controls do not provide complete protection (i.e., most computers), it is ultimately people and their willingness to adhere to security policies that will determine whether systems and organisations remain protected. Users should be educated about:
Anti-virus software must be properly installed and used to give adequate protection, education is again the key. Virus researchers recommend that at least two packages should be used in organisations, one installed in every computer and the other used for confirmation in the EDP department. No anti-virus software is perfect, but by using two packages flaws in one will be covered by the other.
There are many anti-virus software packages, this short article cannot adequately review them. Indeed, unlike general software, where the most important criteria are easily tested or a matter of personal taste, the ability to detect many viruses is difficult to measure. The first requirement is a good library of viruses, which has its own problems ("Analysis and Maintenance of a Clean Virus Library" Vesselin Bontchev, Virus Bulletin Conference, September 1993, p.77-89). Some packages to note are (the version numbers given are the most recent at the time of writing):
Some other anti-virus software, such as Central Point Anti-Virus and the derived Microsoft Anti-Virus distributed with MS-DOS 6.0, has had serious doubt cast on it's ability to protect systems ("The Anti-Viral Software of MS-DOS 6" Y. Radai 1993, Hebrew University of Jerusalem, Israel).
Ultimately, destructive programs are more of an ethical, sociological and legal problem than a technical one. Viruses are designed and released by people, who must have motivation for their malicious work. As their programs are very counter-productive, it would seem no such motive exists; however, the more than 3000 viruses in the wild today make it obvious that there must be many reasons good enough to design a virus. Society must decide if it wishes to continue condone by default the activities of those who write and spread viruses. Other countries (including the U.K. and Sweden) are developing specific laws dealing with viruses. The new Computer Ordinance does not address viruses specifically, no doubt the courts will discover if it provides any protection against them.
Literature on computer viruses