First published: 01st September 1994
By Allan G. Dyer M.Sc.(tech) B.Sc. AIDPM MIAP MHKCS, Head of F-PROT Technical Support, Yui Kee Co. Ltd.
Boot sector viruses are very common, and have caused many of the largest virus incidents, but they have a limited method of infection, and are easily prevented.
To spread, a virus must get executed, so all viruses have a method to make sure they are executed and get a chance to spread. Many viruses (as we will see next month) attach themselves to program files, but the majority of people do not copy programs between machines or continually use new software, so spreading this way is limited. However, every DOS disk, even if it only has data files on it, contains a short program that a virus can use as a host. To see how, we have to take a closer look at the structure of disks.
Disks are divided into circular tracks, and each track is divided into sectors, formatting a disk places magnetic marks on the disk showing where the sectors start and end. The operating system reads these marks and places data in the defined areas. The first sector of a DOS disk is called the Boot Sector. When the disk is formatted, the format program writes a short piece of code to this special sector. The job of this program is to control the PC as it boots up (hence the name, Boot Sector). When a PC is switched on (or after Ctrl-Alt-Del has been pressed), it starts executing instructions from chips fixed inside (the ROM BIOS), these complete various tests and then cause the PC to read the first sector of a disk (the boot sector) into memory and execute it.
Normally, this program looks for parts of the DOS operating system on the disk, loads them and starts DOS running. If the program cannot find a valid operating system, it displays a message like:
Non-system disk or disk error
Replace and press any key when ready
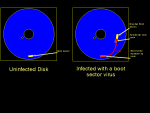
A boot sector virus replaces this program with it's own code (see fig.1). Most boot sector viruses first copy the original boot sector to what they think is an unused sector of the disk, and then write themselves to the actual boot sector. Viruses that are bigger than the size of one sector will store their additional code in another unused area of the disk.
What happens when you boot from an infected disk? First, the boot sector containing the virus is loaded, it then loads the rest of the virus and does it's tasks. Normally, this will be making itself permanently resident in memory so that it can infect every disk used in the machine, and infecting the hard disk. Finally, the virus loads the original boot sector and lets it execute. What does the user see? Nothing unusual, if the disk was bootable, the machine appears to boot normally, if it was not, then the usual message appears, and the user will probably remove the disk and hit a key, so that the machine boots from the hard disk. At this point, however, the virus is resident and it will try to infect every disk used on that machine.
Hard disks are infected in much the same way, but there are important differences. Hard disks have more than one boot sector. Hard disks are often "split" into several partitions, each of which appears to be a separate drive in DOS. Each partition has it's own boot sector, for DOS disks this is called the DOS Boot Record (DBR), plus there is a Master Boot Record (MBR) at the very beginning of the physical disk. The MBR contains the Partition Table, which lists how big each partition is, where they start, and which one should be used to boot from. It also contains a short program that reads the Partition Table and loads the DBR of the appropriate partition.
A boot sector virus might infect the MBR or the DBR of a hard disk. A few, very early, boot sector viruses, like Brain, do not infect hard disks at all. These have largely died out. MBR-infecting viruses are often incorrectly called Partition Table viruses.
A number of boot sector viruses are among the commonest viruses around. The Stoned virus is very well known, it is an MBR-infecting virus that displays the message:
Your PC is now Stoned
on every 8th reboot. Unfortunately, if it infects a non-360KB floppy disk, it is highly likely to overwrite important data, making the disk unusable.
There are very many variants of the Stoned virus, often without the original message. One recent variant is Stoned.Flame (also known as Stamford), this makes a note of the month when it infects a hard disk, and when the month changes it overwrites vital areas of the disk and displays a picture of flashing flames (fig. 2), this has been quite common in Hong Kong recently.
Probably the most famous boot sector virus is Michelangelo, which infects MBRs and formats parts of the hard disk on March 6th (the birthday of Michelangelo Bounnaroti, the famous Renaissance painter). It is structurally similar to Stoned, but will infect non-360KB disks correctly.
The Anticmos virus is an MBR infector that was first found in Hong Kong in January. Two variants are known to exist (A and B), the B variant was first detected in Texas, but was also found in Shenzen within a week. The A variant will wipe the CMOS data of the computer in November, but the B variant merely plays an annoying siren sound on the PC's speaker. The B variant also contains, but does not display, the text:
I am Li Xibin
This hints that it may have been written in Hong Kong or China, and travelled to Texas remarkably fast.
The Form virus is a very common DBR infector that was first found in Switzerland. It contains, but does not display, the text:
The FORM-Virus sends greetings to everyone who's reading this text. FORM doesn't destroy data! Don't panic! Fuckings go to Corinne.
Form stores it's additional code and the original boot sector on the last track of the hard disk, if your disk is very full, FORM might destroy data.
What, then, are the simple protection methods that can be used against boot sector viruses?
Avoid accidently booting from floppy disks. Original PCs always looked for a disk in drive A: before trying to boot from the hard disk. Most PCs now allow the boot sequence to be set, this is done in the Setup options, and is called something like:
Initial System Load: Fixed/Disketteor
System Boot Up Sequence C:, A:When set correctly, the system will always try booting from the hard disk first, ignoring any floppy in drive A.
Create an emergency boot disk containing, along with the operating system, essential tools for disk repair, unformatting, undeletion, virus searching and disinfecting. These will be useful tools in any emergency.
Write-protect your start-up floppy disks, and, indeed, any disks that contain original programs, using the sticky tag over the notch on 5¼" disks or moving the plastic slider to open the hole on 3½" disks. That protection is implemented in hardware, and viruses (or any other program) cannot get around it to write to the disk.
Scan all disks with reliable anti-virus software.
If your anti-virus software has the option, set it to check floppy disks whenever they are accessed and on warm boots.
Data disks are exchanged far more freely and frequently than program disks, many people do not realise that every disk contains a program that can be infected. Everyone accidently leaves a disk in a drive occasionally. It is through these mistakes that boot sector viruses are so successful.