First published: 01st October 1994
By Allan G. Dyer M.Sc.(tech) B.Sc. AIDPM MIAP MHKCS Head of F-PROT Technical Support, Yui Kee Co. Ltd.
File viruses are, perhaps, the simplest to understand, but even here there are many variations to add confusion.
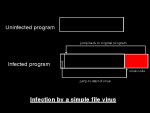
By attaching itself to a program file, a file virus gets executed each time the program is run. It then has a chance to spread to other files. How does the virus attach itself to the program? A parasitic virus writes itself into the program file, often at the end of the program, thus making the file larger (fig.1). It then modifies the beginning of the program to point to the beginning of the addition, and sets a pointer in itself so that it can return to the original program when it has finished.
Some parasitic viruses, called overwriting viruses, are extremely simple, and just overwrite the start of the program. This is not usually a successful infection strategy because infected programs fail to run. Users therefore notice a fault very quickly and call for help, so the virus will normally be cleaned up before it has spread far. In this case, there is no way to disinfect the infected programs, vital parts have been destroyed so they must be restored from backups.
On PCs .COM and .EXE files have a very different internal structure. Parasitic viruses must therefore use different techniques for infecting them, and some only infect one or the other type. One point worth noting is that the names of these files can be changed, say renaming a .EXE file to be a .COM file, DOS will identify the program correctly by it's internal structure, but some viruses just check the extension and will therefore try to infect using the wrong technique. This damages the program, and is another example of how a virus may do unintentional damage through bad design.
A second type of file viruses, the companion virus, uses a feature of the DOS command interpreter to get executed. When a command is typed, DOS first looks for a file of that name with the .COM extension, only if that does not exist will it look for a .EXE file. Companion viruses, therefore, look for a .EXE file, and create a file containing themselves with the same name but a .COM extension. When a command is typed, the virus is executed first, and will usually run the original .EXE file when it is finished. This method of infection is easy to miss - any check of the program files will show none have been changed.
The third type of file viruses, the link virus, has only one example in the wild, DIR II. This virus writes itself to an unused part of the disk once, and then changes the directory entries for all the programs on the disk to point to itself (fig. 2). It keeps a record of the actual locations of the programs so that, each time a program is executed, it can retrieve it correctly so the user does not notice the infection.
These viruses can be further subdivided into memory resident and direct action. Direct action viruses are simpler, the virus loads, does it's work (searches for and infects one or more programs and perhaps tests the trigger condition for the payload) and exits (running the victim program, unless it is an overwriting virus).
When a memory resident virus is run, however, it installs itself into the computer's RAM, usually using the DOS Terminate and Stay Resident (TSR) function. It will remain there until the computer is switched off, and can infect programs as they are run, or copied, or whatever it was designed to do. This is why it is so important to switch your machine off before trying to disinfect a virus, if a virus is in memory it can subvert the operation of your disinfection program in many ways. Incidentally, all boot sector viruses are memory resident, otherwise they would not get a chance to infect other disks and therefore they would not spread.
There are thousands of file viruses, some that I have seen in Hong Kong are:
- Green Caterpillar (Green_Caterpillar.1575.D), characterised by a "caterpillar" that rushes across the screen eating characters.
- Jerusalem (Jerusalem.1808.Standard), first isolated in Israel in 1987, it will delete programs on Friday 13th, and is therefore sometimes known by that name.
- AntiCAD (Jerusalem.AntiCad.4096.Mozart and Jerusalem.AntiCad.2900.Plastique), variants of the Jerusalem virus that are targeted to damage systems using AutoCAD software.
The following viruses were all first reported in Hong Kong, and may have been written here, or in China:
- Nice.A, displays a message starting "Nice to meet you". A slight variant of this (called Nice.B) quickly appeared in Scandinavia and was traced to display driver disks copied in Hong Kong.
- _1099, a virus that showed some new tricks, now known to have at least two variants.
- VTech (Jerusalem.Vtech, Jerusalem.Vtech.2513, Jerusalem.Vtech.2886) a batch of recently appearing viruses that might have been written by a local author or virus writer's group. One variant will overwrite data on the hard disk and corrupt the CMOS information on the trigger date. It also disables Central Point Anti-Virus by deleting key files. This group shows encryption and polymorphism, which will be the subject of a later article.