Computer security has three aspects: Secrecy, Accuracy and Availability. Computer Viruses mostly have an impact on two of these: accuracy, a virus may modify you programs and data, and availability, your machine may not work when you require it.
What are Computer Viruses?
Dr. Frederick Cohen made the definition, "A virus is a program that can 'infect' other programs by modifying them to include a, possibly evolved, version of itself.", he also gives a mathematical definition. However, this definition includes programs that we would not normally call a virus, such as the DOS "DISKCOPY" command, indeed, Dr. Cohen proved using the mathematical form of the definition that any sequence of symbols is a virus in some environment. Clearly, this is not a very useful definition in the real world, and other virus researchers have tried to define "real computer viruses" by referring to a deliberate design to replicate or their spread without permission. For the purposes of this talk, a virus meets Dr. Cohen's definition, AND was deliberately designed to replicate.
Viruses are generally classified by what objects they infect. We will look at the major categories.
Boot Sector Viruses
Boot sector viruses are very common, and have caused many of the largest virus incidents, but they have a limited method of infection, and are easily prevented.
To spread, a virus must get executed, so all viruses have a method to make sure they are executed and get a chance to spread. Many viruses attach themselves to program files, but the majority of people do not copy programs between machines or continually use new software, so spreading this way is limited. However, every DOS disk, even if it only has data files on it, contains a short program in the first sector of the disk that a virus can use as a host.
Normally, this boot sector program looks for parts of the DOS operating system on the disk, loads them and starts DOS running. If the program cannot find a valid operating system, it displays a message like:
Non-system disk or disk error
Replace and press any key when ready
A boot sector virus replaces this program with it's own code (fig.4). Most boot sector viruses first copy the original boot sector to what they think is an unused sector of the disk, and then write themselves to the actual boot sector. Viruses that are bigger than the size of one sector will store their additional code in another unused area of the disk.
What happens when you boot from an infected disk? First, the boot sector containing the virus is loaded, it then loads the rest of the virus and does it's tasks. Normally, this will be making itself permanently resident in memory so that it can infect every disk used in the machine, and infecting the hard disk. Finally, the virus loads the original boot sector and lets it execute. What does the user see? Nothing unusual, if the disk was bootable, the machine appears to boot normally, if it was not, then the usual message appears, and the user will probably remove the disk and hit a key, so that the machine boots from the hard disk. At this point, however, the virus is resident and it will try to infect every disk used on that machine.
Hard disks are infected in much the same way, but there are important differences. Hard disks have more than one boot sector, a "Master Boot Record" that is the first sector on the physical disk, which contains the Partition Table, and a boot record at the start of each partition. For a DOS partition this is referred to as the DOS Boot Record.
A boot sector virus might infect the MBR or the DBR of a hard disk. A few, very early, boot sector viruses, like Brain, do not infect hard disks at all. These have largely died out.
A number of boot sector viruses are among the commonest viruses around. The Stoned virus is very well known, it is an MBR-infecting virus that displays the message:
Your PC is now Stoned
on every 8th reboot. Unfortunately, if it infects a non-360KB floppy disk, it is highly likely to overwrite important data, making the disk unusable.
There are very many variants of the Stoned virus, often without the original message. One recent variant is Stoned.Flame (also known as Stamford), this makes a note of the month when it infects a hard disk, and when the month changes it overwrites vital areas of the disk and displays a picture of flashing flames (fig. 5), this was quite common in Hong Kong last year.
Probably the most famous boot sector virus is Michelangelo, which infects MBRs and formats parts of the hard disk on March 6th (the birthday of Michelangelo Bounnaroti, the famous Renaissance painter). It is structurally similar to Stoned, but will infect non-360KB disks correctly.
The Anticmos virus is an MBR infector that was first found in Hong Kong in January 1994. Two variants are known to exist (A and B), the B variant was first detected in Texas, but was also found in Shenzen within a week. The A variant attempts to wipe the CMOS data of the computer in November, but the B variant merely plays an annoying siren sound on the PC's speaker. The B variant also contains, but does not display, the text:
I am Li Xibin
This hints that it may have been written in Hong Kong or China, and traveled to Texas remarkably fast. The A variant is now common worldwide, and the B variant is beginning to spread in Hong Kong.
The Form virus is a very common DBR infector that was first found in Switzerland. It contains, but does not display, the text:
The FORM-Virus sends greetings to everyone who's reading this text. FORM doesn't destroy data! Don't panic! Fuckings go to Corinne.
Form stores it's additional code and the original boot sector on the last track of the hard disk, if your disk is very full, FORM might destroy data.
File Viruses
File viruses are, perhaps, the simplest to understand, but even here there are many variations to add confusion.
By attaching itself to a program file, a file virus gets executed each time the program is run. It then has a chance to spread to other files. How does the virus attach itself to the program? A parasitic virus writes itself into the program file, often at the end of the program, thus making the file larger (fig. 6). It then modifies the beginning of the program to point to the beginning of the addition, and sets a pointer in itself so that it can return to the original program when it has finished.
Some parasitic viruses, called overwriting viruses, are extremely simple, and just overwrite the start of the program. This is not usually a successful infection strategy because infected programs fail to run. Users therefore notice a fault very quickly and call for help, so the virus will normally be cleaned up before it has spread far. In this case, there is no way to disinfect the infected programs, vital parts have been destroyed so they must be restored from backups.
On PCs .COM and .EXE files have a very different internal structure. Parasitic viruses must therefore use different techniques for infecting them, and some only infect one or the other type. One point worth noting is that the names of these files can be changed, say renaming a .EXE file to be a .COM file, DOS will identify the program correctly by it's internal structure, but some viruses just check the extension and will therefore try to infect using the wrong technique. This damages the program, and is another example of how a virus may do unintentional damage through bad design.
A second type of file viruses, the companion virus, uses a feature of the DOS command interpreter to get executed. When a command is typed, DOS first looks for a file of that name with the .COM extension, only if that does not exist will it look for a .EXE file. Companion viruses, therefore, look for a .EXE file, and create a file containing themselves with the same name but a .COM extension. When a command is typed, the virus is executed first, and will usually run the original .EXE file when it is finished. This method of infection is easy to miss - any check of the program files will show none have been changed.
File viruses can be further subdivided into memory resident and direct action. Direct action viruses are simpler, the virus loads, does it's work (searches for and infects one or more programs and perhaps tests the trigger condition for the payload) and exits (running the victim program, unless it is an overwriting virus).
When a memory resident virus is run, however, it installs itself into the computer's RAM, usually using the DOS Terminate and Stay Resident (TSR) function. It will remain there until the computer is switched off, and can infect programs as they are run, or copied, or whatever it was designed to do. This is why it is so important to switch your machine off before trying to disinfect a virus, if a virus is in memory it can subvert the operation of your disinfection program in many ways. Incidentally, all boot sector viruses are memory resident, otherwise they would not get a chance to infect other disks and therefore they would not spread.
Link Viruses
A link virus can be said to infect the file structure of a disk. It writes itself to an unused part of the disk once, and then changes the directory entries for all the programs on the disk to point to itself (fig. 7). It keeps a record of the actual locations of the programs so that, each time a program is executed, it can retrieve it correctly so the user does not notice the infection.
Macro Viruses
A macro virus is essentially the same in operation as the file infecting virus: running an infected macro results in the virus creating macros that contain copies of the virus code . Macro viruses differ from file viruses by being written using application macro languages (the currently known macro viruses are all written for Microsoft Word 6). A file virus requires that an infected file is run for it to take control, a macro virus requires an infected macro to be run.
Unfortunantly, many applications have features to allow macros to be executed automatically, often leaving the user completely unaware that anything has happened. In the case of WordMacro.Concept, the virus takes advantage of the 'AutoOpen' feature of Microsoft Word.
Short History of Viruses
The flood of viruses we see today is a recent phenomena, but the idea of a program that can produce copies of itself can be traced back to the very earliest stages of Computer Science; in about 1948, John van Neumann (the Hungarian-born mathematician and computer pioneer) wrote a paper on "electronic automata" describing the concept. The idea, however, was little more than an intellectual curiosity. In the late 1970's, some research laboratories experimented with self-replicating programs that could perform routine housekeeping tasks in distributed systems. They quickly found that, once released, these programs would multiply uncontrollably and cause system crashes, so the idea was abandoned.
In 1985, Frederick Cohen completed his thesis on self-replicating programs, he decided to use the term "computer viruses", and gave his now-famous definition. Dr. Fred Cohen is now one of the leading researchers in the field.
The advent of microcomputers gave computing power to millions of people, some of these were interested in how to program them, and some of these new programmers experimented widely, including writing self-replicating programs. The IBM PC became the standard for most computer users, and the conditions had become right for an electronic plague.
It was not until 1987 that the first documented computer virus attack occurred. The virus, which is now called Brain, infected several hundred disks at the University of Delaware, and is reported to have destroyed at least one student's thesis. The writers of the virus actually put their names and address in the virus code. They live in Pakistan, and said they wrote the virus in 1986 'for fun'. They were quite startled to learn that their program had traveled to America within one year. This first attack clearly demonstrated important points:
- Once a virus is "released" by the writer, he looses all control over it. He cannot limit or stop it's spread.
- Viruses can cause damage not intended by their writer. For the Brain virus, the method of infection overwrote a seldom-used section of the disk, this is probably how the student's thesis was destroyed.
The next incident was not long afterwards, a deliberately damaging file virus was found at Lehigh University in November 1987, it became known as the Lehigh virus. Since then, the number of viruses has increased exponentially. Today there are more than 6000 types of virus, increasing by about five every day and there is no sign of the trend slowing down.
Methods of protection
After finding out about the many types of viruses, the vital question is what can we do to stop them?
There is no such thing as a perfect security system, and any product that claims it is perfect should be treated with great suspicion. As a comparison, the President of the United States is probably the best-protected man in the world, but a number of Presidents have been assassinated. In choosing a security system such as anti-virus protection, you must balance the cost and inconvenience of the system against the damage it can prevent. The first rule of computer security is, don't buy a computer. The second rule is, if you do break rule 1, don't turn it on!
How about more practical systems of protection? They can be divided into three parts, Detection, Prevention and Recovery. The earlier you can detect a virus, the less costly the recovery will be. Prevention sounds the best option, we will look at it first.
Prevention
Write Protection
The write protection of diskettes is implemented in hardware, so a virus cannot circumvent it. Write protect your original software diskettes. Most methods of recovering from a virus involve a cold boot from a write-protected diskette known to be clean. If you do not have one, make one now!
Floppy Boot Protection
Boot sector viruses infect your hard disk when you boot from an infected diskette. This usually happens accidently, when a diskette is forgotten in drive A: while the machine is switched on. Avoid accidently booting from floppy disks. Original PCs always looked for a disk in drive A: before trying to boot from the hard disk. Most PCs now allow the boot sequence to be set, this is done in the Setup options, and is called something like:
Initial System Load: Fixed/Diskette
or
System Boot Up Sequence C:, A:
When set correctly, the system will always try booting from the hard disk first, ignoring any floppy in drive A.
Behavior Blockers
Another method of preventing damage by viruses is behavior blockers. These are a resident program that trap key operating system events and give the user the choice of allowing the event or not. Thus, it would warn on attempts to write EXE or COM files, or formatting a disk. These generally tend to be too cumbersome and unreliable to be useful. They require the user to make an informed decision on each event, many users are not suitably knowledgeable, and the repetition of questions leads to an automatic OK, or the removal of the protection software entirely.
A general problem with simply preventing a virus from affecting our system is that the virus remains a disaster waiting to happen. It may affect our system later, when the protection has been removed for some reason, or it may affect someone elses system. Either way, it is better in the long run to detect and remove the virus.
Detection
Signature Scanners
Many anti-virus packages use signature scanning. This involves selecting a part of the virus code and searching for it in programs. Signatures must be selected and tested carefully, many viruses have been modified specifically to avoid a particular scanner. Choosing a signature in a critical area of the virus can make such a change more difficult. Conversely, a signature may also occur in some innocent software, causing a false positive. Regional software, such as Chinese language software, can be more prone to such false positives because of a lack of opportunity to test new versions if a foreign software producer does not have a good network of beta-test sites.
Signature scanning is fairly well understood by some virus writers, and various attempts have been made to avoid it. The most complex method is used by the polymorphic viruses. Against these an advanced extension of signature scanning, best described as algorithmic scanning, is used. This searches for a common pattern in the decryption routines.
Heuristic Scanners
A great weakness of signature scanners is that they only detect known viruses. In fact, a well-designed signature scanner can detect many variants, and since most new viruses are variants of others this is often sufficient. Heuristic scanners, rather than looking for a particular signature, look for virus-like code and can therefore find entirely new viruses. This results in a potentially greater chance of false positives, but careful refinement has produced some reliable examples.
Integrity Checking
Another approach to finding viruses is to look for programs that change. If a program changes unexpectedly, maybe a virus did it. This method is used by checksumming programs, and it is very secure. It is equally good at catching known and unknown viruses. Some of the more advanced checksumming programs can often repair the changes made. However, checksumming must be installed before a virus has attacked. The initial installation should be performed after a scan with an up-to-date scanner. Additionally, checksummers are vulnerable to slow viruses and a stealth virus active in memory can also fool them.
Active Detection
A checksumming or scanning program that is run occasionally to check a system is clean is limited because it cannot prevent infection. A scanner used on all incoming software and disks can stop infection at source, but program or disk may be forgotten or skipped. Resident versions of both methods exist. These scan or checksum each executable as it is run, and prevent execution if a virus or a change, respectively, is found. These have a permanent impact on system performance and memory, programs will take slightly longer to load. Security is balanced against speed and reduced size, a resident anti-virus program is useless if the machine runs too slowly or has too little memory for productive work. The situation here is worst with TSR's in DOS, more advanced operating systems, such as OS/2 and Windows, allow more powerful resident protection.
To avoid the memory overhead of a checksumming resident program, some packages offer a method, sometimes called inoculation, of making programs self-checking. The package adds code to other programs to perform a check as they start. This modification is virus-like in many ways, and an unaware scanner or a checksummer would give a false positive. Some programs already have self-checking built in, and would naturally object to such modification. Additionally, if the inoculation is inadvertently performed on already infected software, many scanners would not be able to see past the inoculation and detect the virus.
Recovery
Once a virus has been detected, the system must be restored to a clean state.
Backups
The safest method is replacement of the affected software from a clean backup or reinstallation from uninfected original diskettes.
Disinfection
Many viruses can be safely removed, saving time and trouble. It has already been mentioned that some checksumming programs, by virtue of their knowledge of the original form of the program, can do a repair. Also, scanners often have a cleaning module, either integral or as a separate program. Here, specific knowledge of how a particular virus infects is used to remove it. It is most important that the identification of the virus is accurate, many slight variants exist, and attempting to remove the wrong variant might also cut out some of the original program code.
Damage Assessment
Even after a virus has been removed, damage caused by it may remain. Some viruses cause deliberate, random corruption to data files. For this reason, it is best to identify the virus and check what it does.
The Situation Today
Viruses in Hong Kong
What viruses have been seen in Hong Kong?
- AntiCad.2900.Plastique.A
- AntiCad.4096.Danube
- AntiCMOS.A
- AntiExe
- Burger.560.AY
- Burger.560.BA
- Cascade.1701.A
- Crazy_Lord
- Dalian
- Green_Caterpillar.1575.A
- Green_Caterpillar.1575.D
- Green_Caterpillar.1575.H
- Jerusalem.1808.Standard
- Jerusalem.Clipper
- Jerusalem.CVEX.5120.A
- Jerusalem.HK.2358
- Jerusalem.HK.2513
- Jerusalem.HK.2880
- Jerusalem.HK.2886
- Jerusalem.Sunday.A
- June_12th
- Keypress.1232.A
- Liberty.2857
- Line
- New or modified variant of Little_Red
- MacGyver.2824.A
- Mange-tout.1099
- Ming.1017
- Ming.491
- Ming.CLME.1528
- Ming.CLME.1952
- NRLG.1030 - Generation 1
- NRLG.776 - Generation 1
- NRLG.992 - Generation 1
- One_half.3544
- Ping-Pong.Standard
- Possibly a variant of Devil's_Dance
- Quartz
- Sampo
- Sblank
- Shatin
- Shutdown.644
- Shutdown.698
- Stoned.Dinamo
- Stoned.Empire.Monkey.D
- Stoned.Flame
- Stoned.NoInt.A
- Stoned.Standard
- Timid.305
- TV
- Vienna.648.Reboot.A
- Yankee_Doodle.TP.44
- Yankee_Doodle.TP.44.E
This is a table compiled from samples I have been sent. But there are viruses here that are quite old, and new viruses that have never been seen "in the wild". So what viruses are you likely to find attacking your organisation in Hong Kong? This is a shorter list (Table 2) of cases where the virus seemed to be spreading . This reflects the international situation, most actual virus incidents are caused by a small number of viruses:
- Boot Sector Viruses
- AntiCMOS
- AntiEXE
- B1
- Buptboot
- Form
- LZR
- Sampo
- Stoned.Empire.Monkey.A
- Stoned.Flame
- Stoned.Standard
- Swiss_boot
- V-sign
- W-boot.A
- File Viruses
- Dailan
- Die_Hard
- Jerusalem.HK.2358
- Jerusalem.HK.2886
- June-12th
- MacGyver.2824.A
- Ming.491
- Ming.CLME.1952
Even more significantly, if we look at the numbers of boot sector and file viruses we find most incidents are caused by boot sector viruses (fig. 14). Note here that file viruses are more common in a home environment. If you think about how file viruses are transmitted, an executable file must be transferred, it becomes clear why this is so, business users exchange documents frequently, but programs rarely. Home users are often enthusiasts who freely swap programs, often via BBSs with people they do not know.
Macro Viruses and the Future
Viruses are often seen as a DOS problem, which will disappear when people move to real operating systems. It is argued that DOS is full of security loopholes, and a better operating system will eliminate viruses. In fact, this is totally incorrect. We have already seen that the idea of a self replicating program and some early examples existed before the first PC was built or DOS 1.0 was written. Many DOS viruses will happily spread under Windows, Win 95, NT or OS/2. Also, it is entirely possible to write a virus for these operating systems, and for other, novel, environments.
Macro Viruses: The new threat
The new threat is actually quite old, anti-virus researchers have been discussing the possibility since 1989 , . The only suprising feature is that it took the virus writers so long to find the idea.
It was the Winword.Concept virus that hit the news in August, but since then, three other macro viruses have been found. One of them attempts to drop a conventional file virus, it fails, because there are three programming errors, but these could all be fixed quite easily.
There are a number of important points:
- Macro viruses are not just a problem for MS Word, any reasonably powerful macro language can be used
- Macro viruses are very easy to modify
- Current A-V scanners can detect them, BUT
- Every file will need to be scanned, without knowing the file formats for these applications, scanning will be slow.
Users can assist in this, ask your application developer to:
- think of security when designing applications, allow features like autoexecute macros to be switched off, or selective installs that do not install unrequired features.
- co-operate with anti-virus developers, make the file formats public so that the files can be searched quickly and efficiently.
Macro viruses change the way we need to think about viruses. We used to say that viruses cannot spread from data files, and you cannot spread a virus just by reading email, you must execute something.
| Old Rule | The Change | New Rule |
|---|
| A virus cannot spread from a data file | Documents can contain executable code | Macro viruses infect documents |
| You cannot spread a virus just be reading email | Mail readers start viewers automatically | Macro viruses can spread when you open an infected message |
Viruses can now infect documents, because a document can contain executable macro code. Viruses can infect your system when you read email, if someone sends you a document via email, your mail reader might automatically start an application when you read that, so a macro virus can infect your system just when you read mail. Confusingly, the line between data and programs and the line between reading and executing has been blurred, a document can contain executable code, and a mail read may imply execution of an embedded macro.
An Anti-Virus Strategy
Viruses are a concern for the whole organisation, and should be planned for accordingly. Case studies show that outbreaks can be exacerbated by distributed organisation structures and later reinfections are common.
Appoint an Administrator: This person will be responsible for the day-to-day monitoring of viruses in the organisation. He will have detailed knowledge of how viruses spread and the risks posed by different sorts of infection. This is a similar position to a fire safety officer, who may order people out of a building in an emergency. The anti-virus administrator has high authority and may order computers to be quarantined or shut down.
Prepare the Anti-Virus Strategy: The administrator will have a major input into this.
Choose the anti-virus software: Apart from the obvious criteria of detecting the most viruses, also consider the features that make it easier to administer the situation throughout your organisation: Can updates be distributed automatically, can the administrator receive reports from infected machines automatically, can it be configured to scan without user intervention? Does it fit your anti-virus strategy?
Implement basic precautions: Backups are a traditional method of data protection that are still useful in protecting against viruses, but if a machine has been infected for some time, all the backups could be infected as well. We have already discussed a very effective trick to use against boot sector viruses.
Define the role of staff: write an Anti-Virus code. This must be clear and simple, here is an example.
An Anti-Virus Code (Example)
It is the responsibility of all computer-using employees to watch for computer viruses and prevent their spread by following this code:
- All virus incidents, or suspected incidents should be reported to the AV administrator (Mr. J. Chan ext. 234)
- All disks entering the company from any source should be scanned using the latest version of the company's standard AV software.
- All PCs must have the company's standard AV software installed. This must not be disabled or removed for any reason. If the software is interfering with other work or behaving abnormally, contact the AV administrator.
- Always remove diskettes from drives before rebooting (unless you are intentionally booting from a diskette that has been scanned clean).
- If your machine or software behaves abnormally, contact the AV administrator or technical support for advice.
Train staff: Education of users is vital . For most staff, a one-hour session that introduces the dangers of viruses, the company anti-virus code and the basics of the anti-virus software chosen could be sufficient. Other staff, particularly technical staff, would require more training. Their position of power, particularly in a networked environment, makes it more devastating when their machine is infected. (a properly configured network is quite resistant to virus spread, until the supervisor logs in and executes an infected program!)
Keep aware of the threat: Monitor the number of incidents, and be aware that viruses are a moving target, macro viruses are just one example of how the virus situation can change radically.
Summary
The objective of every organisation is to reduce the cost of virus incidents. This goal can be achieved by implementing a suitable anti-virus strategy. Good anti-virus software is one component of the strategy (fig. 19).
References
- Frederick B. Cohen, 'A Short Course on Computer Viruses', second edition, Chapter 1, John Wiley & Sons Inc., (1994)
- Frederick B. Cohen, 'A Short Course on Computer Viruses', second edition, Appendix B, Theorem 5, John Wiley & Sons Inc., (1994)
- 'Frequently Asked Questions on Virus-L/comp.virus', Release 2.00, section B1, maintained by Nick FitzGerald, (1995)
- Richard Ford, 'Macro Viruses: The Sum of All PH33RS?', Proc. 5th Int. Virus Bulletin Conference, pp.I-VI, (1995)
- Allan Dyer, 'Recent Viruses, Virus Writers and Routes of Virus Spread in Hong Kong and China', Proc. 5th Int. Virus Bulletin Conference, pp.151-158, (1995)
- 'WildList - PC Viruses in the Wild', collated by Joe Wells, (1995)
- Harold Highland, 'A Macro Virus', Computers & Security 8, pp.178-188 (1989)
- Vesselin Bontchev, 'Future Trends in Virus Writing', Proc. 4th Int. Virus Bulletin Conference, pp.65-82 (1994)
- Jean Hitchings, 'Human Dimension of Computer Viruses', Proc. 5th Int. Virus Bulletin Conference, pp.21-27, (1995)
- Paul Ducklin, 'Blessings in Disguise: Building Out of Disaster', Proc. 5th Int. Virus Bulletin Conference, pp.11-20 (1995).
- Paul Ducklin, 'Anti-Virus Education: Have We Missed the Boat?', Proc. 4th Int. Virus Bulletin Conference, pp.27-36 (1994)
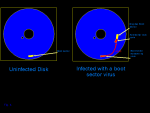 Fig. 4: Infection of a diskette by a boot sector virus hi-res
Fig. 4: Infection of a diskette by a boot sector virus hi-res Fig. 5: Screenshot of the Flame boot sector virus hi-res
Fig. 5: Screenshot of the Flame boot sector virus hi-res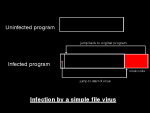 Fig. 6: Infection by a simple file virus hi-res
Fig. 6: Infection by a simple file virus hi-res Fig. 7: Infection by a link virus, such as DIR II hi-res
Fig. 7: Infection by a link virus, such as DIR II hi-res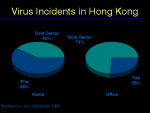 Fig. 14: Virus Incidents in Hong Kong hi-res
Fig. 14: Virus Incidents in Hong Kong hi-res Fig. 19: A successful Anti-Virus Strategy hi-res
Fig. 19: A successful Anti-Virus Strategy hi-res